Social Engineering Likely Cause of Yahoo! Hack

The FBI believes that the massive Yahoo! breach started with either a social engineering or spear phishing attack on privileged users according to Ars Technica.
“Malcom Palmore, the FBI special agent in charge of the bureau’s Silicon Valley office, told Ars in an interview that the initial breach that led to the exposure of a half a billion Yahoo accounts likely started with the targeting of a ‘semi-privileged’ Yahoo employee and not top executives. He said social engineering or spear phishing ‘was the likely avenue of infiltration’ used to gain the credentials of an ‘unsuspecting employee’ at Yahoo.”
Social Engineering and Spear Phishing Now Preferred Attack Technique
What we see here is very sophisticated hackers working for the Russian government used social engineering techniques to perpetrate the biggest hack in history. They didn’t use network penetration tools or malware or other sophisticated attacks that government agencies have ready access to. They simply acquired privileged user credentials through social engineering and then moved directly to the data they valued.
The FBI doesn’t say much on the record. When they say social engineering “was the likely avenue of infiltration,” they are giving themselves plausible deniability using the modifier “likely,” but telling you what they really know. They are also indirectly offering a warning that this can happen to others.
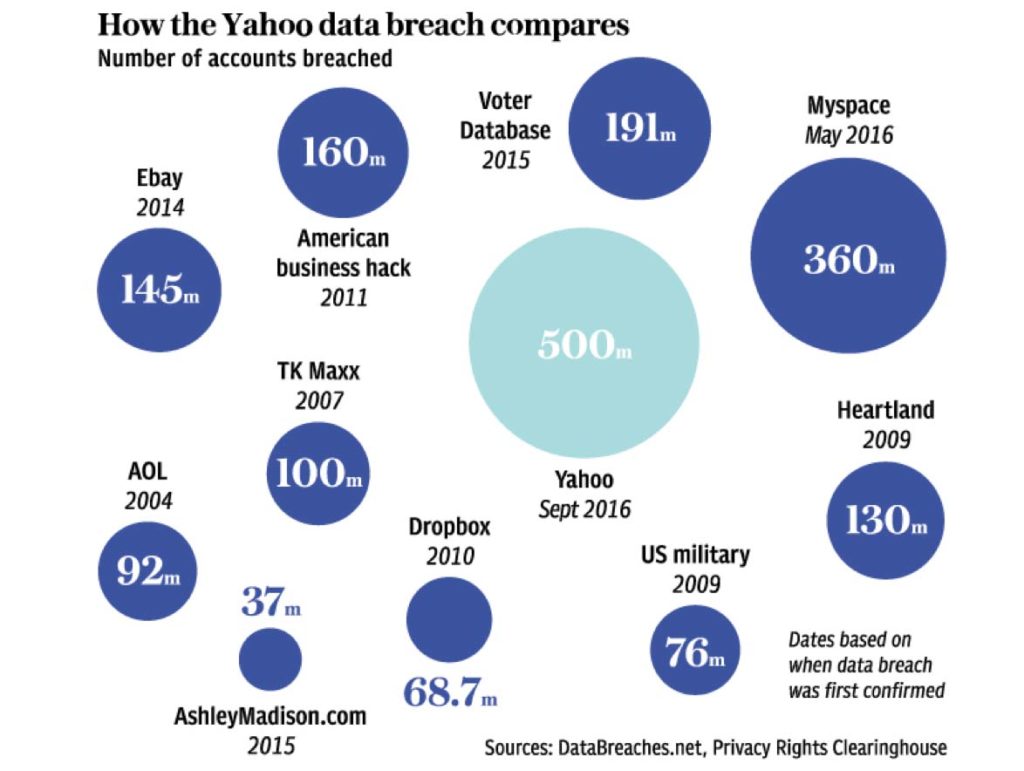
The 5 Agonies Social Engineering Inflicted on Yahoo
We recently documented the 5 Agonies of Social Engineering Cyber Attacks and Yahoo was certainly hit by all five categories.
- Direct costs: This is unclear. It doesn’t appear there will be any credit monitoring for users, but we know that the company is now subject to 43 class action lawsuits and may be subject to SEC fines.
- Recovery costs: In addition to fees paid for incident response, there will likely be new costs for software.
- Lost productivity: There is no estimate today, but you can be sure the number of hours lost from this are large. Everyone from the company board of directors to the IT department were drawn into this and likely many other managers.
- Business disruption: Yahoo started losing email users right after the announcement which means fewer page views to monetize through advertising, its primary revenue source.
- Damaged reputation: After revelations of the breach surfaced, Verizon reduced its acquisition price for Yahoo by $350 million.
This is a big breach and many of the costs are not clear today. However, if it were only $350 million, that means 6.8% of 2016 revenue and 40% of company EBITDA vanished. Then again, we know the total costs will be far higher than this single acquisition mark-down.
Business Email Compromise is Widespread and Costly

Yahoo is only one recent example of a cybersecurity breach that originated from social engineering or spear phishing. These techniques are increasingly used by hackers because they work. The FBI calls this a Business Email Compromise (BEC) attack and there were 17,642 victims in the U.S. between October 2013 and February 2016. The reported cost of these attacks was $2.3 billion giving us an average loss of $130,000 per incident, but many run into the millions. Even the most sophisticated cybersecurity defenses don’t protect you from attacks where your employees unwittingly allow cyber attackers to gain access to your data and networks.
What Can You Do About Social Engineering and Spear Phishing?

We know that phishing training helps protect organizations against less than one-third of spear phishing and social engineering attacks. An automated solution that proactively protects employees from falling for these scams is needed to fill the cyber defense gap. Graphus has developed a solution for G Suite users that automatically eliminates social engineering and spear phishing attacks before your employees click on links or reply to nefarious emails that look all too legitimate. We have been at this a long time and have just spent 15 months proving the technology with ten companies in a private beta period.
The solution identifies trusted relationships between users by applying graph theory, machine learning and big data algorithms. There is a lot of talk today about machine learning and this is a practical application that can be applied to protect companies today.
Graphus can be activated by G Suite users in about a minutes and immediately start protecting your employees from social engineering and spear phishing delivered through Gmail. G Suite security does provides some protection, but not enough. Steve Morgan from Cybersecurity Ventures commented last week, “bad mail that gets through is wreaking havoc on email accounts — and contributing to the cybercrime epidemic that is costing the world trillions of dollars annually.”
You can start a free Graphus 30-day trial today or learn more by clicking the buttons below.










