The “Five Agonies” of Social Engineering Cyber Attacks

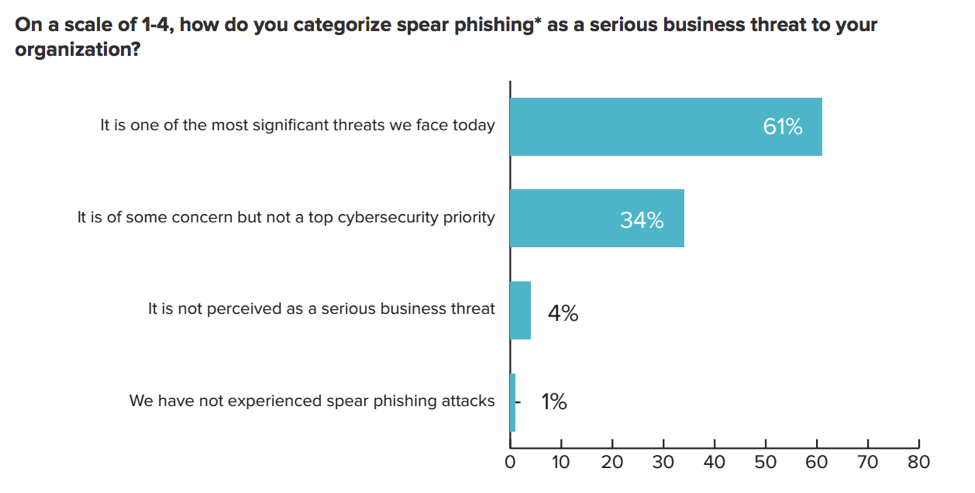
A 2016 survey by Information Security Media Group found that 60% of businesses suspected they were targets of social engineering attacks in the previous 12 months. Of those companies, 65% confirmed that employee credentials were compromised as a result of the incidents. Another 61% of companies reported that spear phishing was “one of the most significant threats we face today.” These attacks aren’t going away. Cyber attackers use social engineering and spear phishing because they work.
The Costs Are Bigger Than You Think
FBI data show that social engineering attacks cost companies an average of $130,000 with damages climbing into the millions of dollars for many companies. However, any victim of a cyber attack will tell you that these losses are only a portion of the damage sustained. There are up to “Five Agonies” inflicted by successful cyber attacks.
- Direct financial loss
- Recovery cost
- Lost productivity
- Business disruption
- Reputation damage
How Many Agonies Will You Endure?
You can guarantee that every successful cyber attack, no matter how minor, will result in some lost productivity. Someone must resolve the issue, make a change or deal with a delay. If you catch the attack early, lost productivity might be your only damage. Attacks that are caught late often involve multiple agonies that make the incident even harder to absorb.
This means that every successful attack includes between one and five of the agonies. In our list, we order them based on what people think about first when confronting the risk of cyber attack. The reality is that the severity of impact is often the exact opposite order. While the direct financial loss and recovery costs are often paid for in the quarter they occur, business disruption and reputation damage may undermine company finances for months or years.
The Five Agonies represent what you are protecting the organization against. The cyber criminals may simply want your money or secrets, but the damage typically extends well beyond cash. To protect your organization, you must first protect your people from themselves. Social engineering, spear phishing and related techniques target your weakest cybersecurity link, your employees. Let’s discuss the agonies first.
Direct Financial Loss

The most prominent agony is direct financial loss. This is what drives the captivating headlines. It is typically easily measured and often relates directly to the cyber criminal’s take from the attack. Social engineering and phishing scams are highly effective. They have even spawned a new technique called Whaling where CEOs and CFOs are targeted directly. Damages tend to range from a low end of $25,000 to multi-million dollar losses.
Recovery Cost

Calculating recovery cost is also relatively straightforward. The organization paid an incident response team to clean up after an attack. New software is purchased to resolve the compromise and protect against future intrusions. Credit monitoring is purchased for affected customers. These are invoices you can add up. This is the second most common cost after productivity loss. Many incidents don’t actually result in stealing company funds or ransoming data but result in data loss that lead to business secrets or customer information being auctioned to bidders in the dark web.
Productivity Loss

Every cyber attack involves some productivity loss. Often, it is substantial and hard to fully document. Countless meetings, employee updates, customer communications, and other activities extend well beyond the IT or security teams. Every minute employees spend on discussing or taking steps related to a cybersecurity breach represents time not directed towards operating the business.
Business Disruption

Productivity loss measures the impact on people’s time and attention. Business disruption is about impacts to your customers and supply chain. If your equipment can’t operate, you may need to run overtime shifts to make up for delays. If you can’t ship product from your warehouse, you may miss your quarterly revenue target or spend time expediting shipments to make up for the delays. Anxious customers may try a supplier that can provide competing products immediately. After a breach, your bank and insurance company may ask to audit your security practices. Security incidents that disrupt business operations can have long lasting impact.
Reputation Damage

It is very difficult to regain trust from customers and suppliers after you have had a significant cybersecurity incident, especially if it was well publicized. Is your trust in a supplier shaken when they have been breached and potentially lost confidential information about your business? It is a natural reaction and can undermine a company’s reputation for years.
Preventing Agony in Your Business
So, how do you avoid the 5 Agonies? Implementing comprehensive security can be a daunting task. A particular challenge is defending against attacks that originate through email, compromised websites and malware accessed through cloud-based productivity applications.
The FBI reported 17,642 victims of business email compromise between October 2013 and February 2016. The reported cost of these attacks was $2.3 billion giving us an average loss of $130,000 per incident. But, readers of this post know that is only part of the cost since direct financial loss is one of five agonies these businesses sustained.
You can lock down your network, but can you really keep your people from communicating with customers, suppliers and partners? Not a chance. That means we can secure all the windows with the latest cybersecurity tools, while cyber attacks come through the front door courtesy of unsuspecting employees. This is where Graphus can help.
Automated Protection Against Social Engineering Attacks
Graphus employs graph theory, machine learning and big data algorithms to identify trusted relationships between your employees and the people they communicate with. At the same time, the solution automatically identifies and eliminates known and newly identified dangers. We know that about 65% of spear phishing attacks are successful even after employees have been trained to identify phishing emails. People are easily fooled. Graphus is not.
You can forget about the fancy technology we use to protect your organization against social engineering and spear phishing. All you really need to know is:
- You can activate Graphus for G Suite in less than one minute
- Graphus starts protecting your organization immediately
- It just works
Nearly twenty years of hard-earned expertise working with DNS, threat intelligence, graph theory, big data and machine learning has been packaged into a simple, powerful automated system that anyone can use. There is even a dashboard that shows you exactly what is going on, where you are being attacked and how to investigate further. However, you don’t need to even look at the dashboard. Graphus protects you automatically.










