Cyberattacks on Critical Infrastructure Are Surging

The technology boom has brought a plethora of innovative solutions and services into the world and our daily lives. But all those solutions depend on digital technologies like the internet and wifi signals to work. Even our critical infrastructure greatly depends on digital systems. A significant interconnectedness between these systems enables the smooth delivery of water, power, healthcare, food and other critical infrastructure components. However, that increased connectivity comes with a price, and the danger posed by cyberattacks on these strategic objectives looms large. New cyberthreats are emerging regularly, making the critical infrastructure of nations and organizations vulnerable on new fronts.

Is your email security solution really getting the job done? This checklist helps you find out! GET CHECKLIST>>
A lack of adequate access controls creates dangerous vulnerabilities
An attack on critical infrastructure can cripple nations and organizations. Plus, a cyberattack on one critical infrastructure sector can cause cascading second-order effects on other critical infrastructure sectors, leading to a large-scale catastrophe. According to the annual 2022 IBM Cost of a Data Breach Report, among 550 organizations that were studied across various industries, 83% have had more than one data breach. The same report also reveals that ransomware and destructive attacks represented 28% of breaches amongst critical infrastructure organizations studied, highlighting how threat actors aim to fracture the global supply chains that rely on these organizations.
The same IBM report points to a failing onthe part of many critical infrastructure organizations that creastes a dangerous vulnerability that is easy for bad actors to exploit. Many critical infrastructure organizations lag in implementing zero trust architecture, a best practice to reduce cyberattack risk that has been recommended by a variety of experts including Microsoft and The U.S. Cybersecurity and Infrastructure Security Agency (CISA). Zero trust establishes strong access controls that keep cybercriminals from making use of phished or stolen passwords through authentication procedures. Almost 80% of critical infrastructure organizations studied don’t adopt zero-trust strategies, registering average breach costs rise to $5.4 million – a $1.17 million increase compared to those that do.

Get the guide that helps you detect & defeat dangerous BEC attacks to keep your company out of trouble! DOWNLOAD IT>>
Critical infrastructure is under siege by ransomware gangs
CISA delineates 16 critical infrastructure sectors. In 2021 14 of those 16 critical infrastructure sectors fell victim to ransomware attacks. IBM’s X-Force Threat Intelligence Index 2021 drilled deeper into the industrial and infrastructure cybersecurity space to determine which industries that rely on operational technology (OT) came under siege the most in 2021. Their researchers determined that the manufacturing sector replaced financial services as the top attacked industry in 2021, victimized in 23.2% of the attacks X-Force remediated last year.
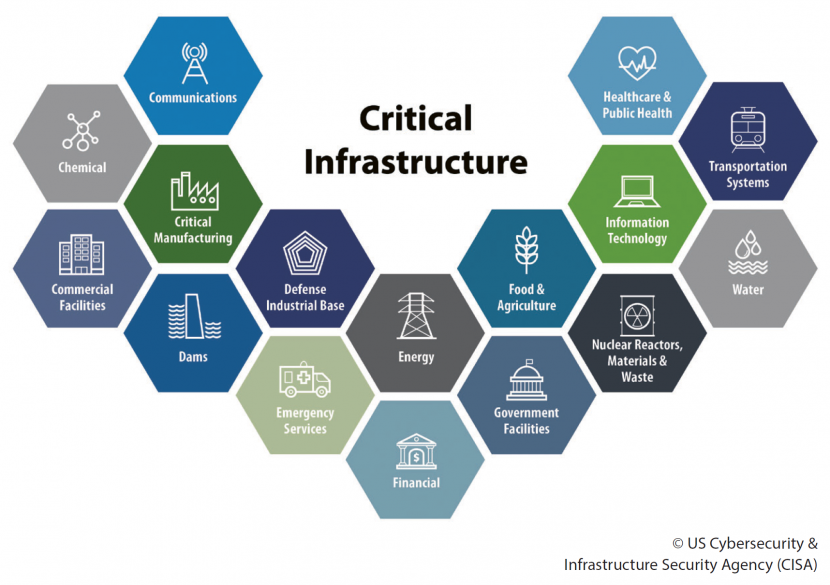
Source: CISA

Learn how incident response planning boosts cyber resilience & security. GET THE EBOOK>>
3 critical infrastructure sectors are especially prone to cyberattacks
Cyberattacks are a danger for every organization that forms part of the world’s critical infrastructure, but a few sectors have been having an especially challenging time in the last few years, including these three.
Healthcare: The healthcare industry has witnessed a sharp spike in cyberattacks in recent years, targeting several hospitals and other healthcare facilities. According to the annual 2022 IBM Cost of a Data Breach Report, a healthcare data breach now comes with a record-high price tag—to an average of $10.1 million. These cyberattacks cause significant financial damage to healthcare systems as they often struggle to mitigate the costs of data breaches. An instance is the devastating attack on Universal Health Services that took down all its IT systems, leading to a network shutdown at 250 of its hospitals around the country. The attack cost the health company almost $67 million in lost revenue and recovery.
Food and Agriculture: The Federal Bureau of Investigation (FBI) has recently issued a warning for the food and agriculture (FA) sector that ransomware actors may attack agricultural cooperatives during critical planting and harvest seasons, disrupting operations, causing financial loss, and negatively impacting the food supply chain. The FBI report also states that six grain cooperatives faced ransomware attacks in the fall of 2021. Cybercriminal gangs used a variety of ransomware variants, including Conti, BlackMatter, Suncrypt, Sodinokibi and BlackByte, which forced some victims to halt production while others lost administrative functions completely.
Energy: The modern world relies heavily on the energy sector to meet energy and fuel requirements. It ensures the smooth functioning of many other critical infrastructure sectors, such as transportation and electricity generation is hard to imagine if the energy sector faces disruptions in its operations. That’s why the energy sector has recently become a hotbed of cybercrimes. According to an S&P Global Energy Security Sentinel, a total of 45 cybersecurity incidents targeting energy and commodities infrastructure have taken place since 2017, and thirteen of these have taken place in this year, the highest annual level over the last six years. Additionally, a recent investigation by Trend Micro has found that 89% of electricity, oil & gas, and manufacturing firms have experienced cyber-attacks impacting production and energy supply over the past 12 months.

Are you ready to stop ransomware? Find out with our 5 Steps to Ransomware Readiness infographic! GET IT>>
The danger of nation-state cybercrime against critical infrastructure is real
It is not only the increasing number of cyberattacks on critical infrastructure by run-of-the-mill cybercriminals that raises concerns. Some governments are using ransomware to conduct cyberwarfare against other countries. This situation is more alarming as cyberattacks sponsored by nation-states are conducted by well-funded and competent operators and aimed at disrupting another nation’s critical infrastructure. A recent study by Trellix and the Center for Strategic and International Studies (CSIS) revealed that nearly nine in 10 (86%) organizations believe they have been targeted by a nation-state threat actor.
Nation-state cybercrime has become a cause of worry as more and more countries started launching cyber warfare on other countries. The ongoing conflict in Eastern Europe between Russia and Ukraine is a prime example of this type of conflict. Russian cybercrime groups have been relentlessly targeting the critical infrastructure of Ukraine. One of the most dangerous attacks is the wiper attack against KA-SAT network of Viasat. In its official statement, Viasat confirmed that the cyberattack overwrote critical data in their internal memory, rendering tens of thousands of modems across Europe inoperable. The severity of the attack was such that it even impacted modem services in France and Italy and paralyzed wind turbines in Germany, according to several published reports.
Meanwhile, cyberattacks on Iran’s state-owned Khuzestan Steel Co. and a credential compromise attack on The Shin Bet (Israel Security Agency) highlight the prevalence of nation-state cybercrime in other conflict-prone regions. In another nation-state incident, researchers identified campaigns by two North Korean government-backed groups targeting employees across numerous media, fintech and software companies. The hackers used phishing emails advertising fake job opportunities and exploited a vulnerability in Google Chrome to compromise the companies’ websites and spread malware.
Explore today’s biggest threats & what’s next in The State of Email Security 2022 GET IT>>
Graphus protects critical infrastructure against cyberattacks
With a monumental rise in cyberattacks, cybersecurity is no longer an option for organizations; it is a dire necessity. Cybercriminals lurk like hawks, ready to pounce on the tiniest opportunity to launch sophisticated email-based cyberattacks on organizations. Unfortunately many organizations still rely solely on traditional email security solutions, but they can’t stand up to the test. Graphus can.
Graphus is the world’s first automated phishing defense platform that protects organizations from even the most sophisticated email-borne attacks. Leveraging its patented AI technology, Graphus automatically detects phishing emails, putting three layers of defense between a phishing email and your organization. Graphus automatically monitors communication patterns between people, devices and networks to reveal untrustworthy emails, making it a simple, powerful and cost-effective automated phishing defense solution for companies of all sizes.
Here are some of the features that make Graphus the best email security solution:
- Block sophisticated phishing messages from reaching employees
- Put three layers of protection between employees and phishing email messages
- Seamlessly deploys to Microsoft 365 and Google Workspace via API, without big downloads or lengthy installs
- Provide intuitive administration and precise reporting to help you gain insights into the effectiveness of your security, level of risks, attack types and more
Book of demo of Graphus to start your email security journey.










